- LogonBox VPN 2.4.14 – Now Available
 by Lee PainterIntroduction LogonBox is pleased to announce the immediate availability of LogonBox VPN 2.4.14. This release includes support for Duo’s new CA certificate pinning bundle and the ability to load new server SSL certificates without requiring a server restart. The changelog at the bottom lists all new features and bugs fixed.
by Lee PainterIntroduction LogonBox is pleased to announce the immediate availability of LogonBox VPN 2.4.14. This release includes support for Duo’s new CA certificate pinning bundle and the ability to load new server SSL certificates without requiring a server restart. The changelog at the bottom lists all new features and bugs fixed. - LogonBox SSPR 2.4.14 – Now Available
 by Lee PainterIntroduction LogonBox is pleased to announce the immediate availability of LogonBox SSPR 2.4.14. This release includes support for Duo’s new CA certificate pinning bundle and the ability to load new server SSL certificates without requiring a server restart. The changelog at the bottom lists all new features and bugs fixed.
by Lee PainterIntroduction LogonBox is pleased to announce the immediate availability of LogonBox SSPR 2.4.14. This release includes support for Duo’s new CA certificate pinning bundle and the ability to load new server SSL certificates without requiring a server restart. The changelog at the bottom lists all new features and bugs fixed. - Benchmarking WireGuard: Why Your Data Plane Location is Critical for Speed
 by Lee PainterWireGuard is celebrated worldwide for its lean code base and superior speeds compared to legacy protocols like OpenVPN. But if your team is still facing sluggish remote access, the problem isn’t the protocol—it’s the architecture. The single greatest factor affecting VPN speed is latency, and latency is primarily determined by distance. While using WireGuard guarantees… Read more: Benchmarking WireGuard: Why Your Data Plane Location is Critical for Speed
by Lee PainterWireGuard is celebrated worldwide for its lean code base and superior speeds compared to legacy protocols like OpenVPN. But if your team is still facing sluggish remote access, the problem isn’t the protocol—it’s the architecture. The single greatest factor affecting VPN speed is latency, and latency is primarily determined by distance. While using WireGuard guarantees… Read more: Benchmarking WireGuard: Why Your Data Plane Location is Critical for Speed - Hybrid VPN: Cloud Management, Zero Data Traffic
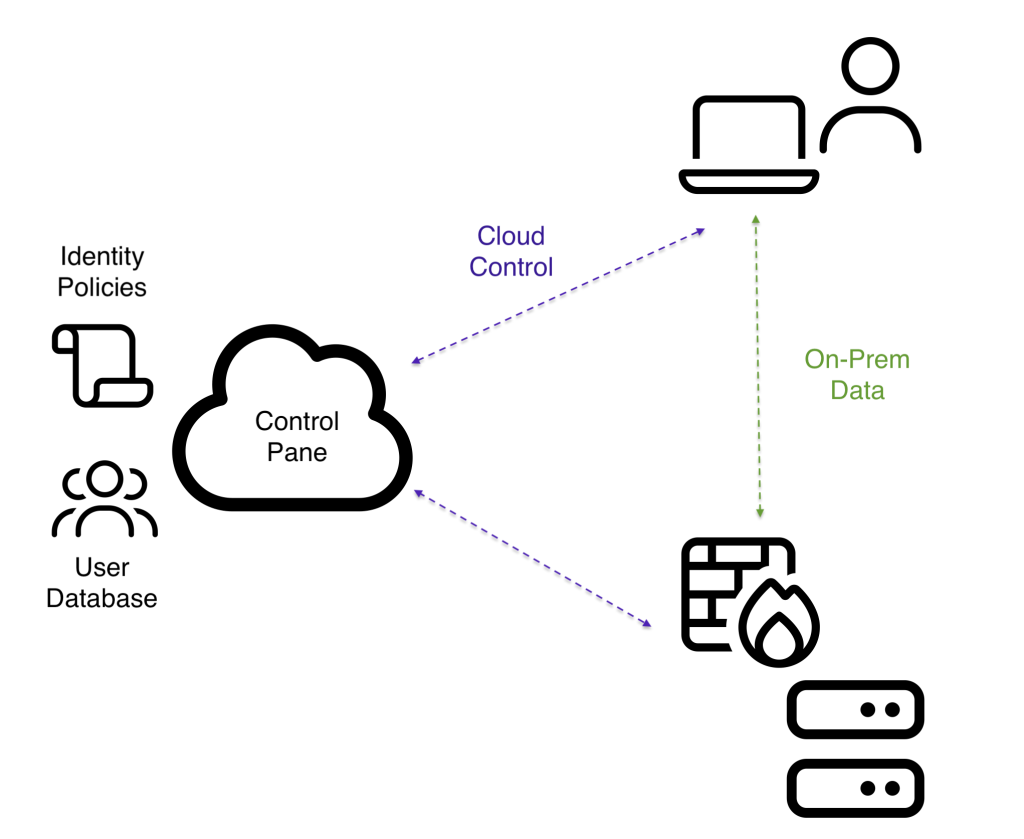 by Lee PainterThe shift to cloud-managed VPNs often forces IT administrators to choose between management convenience and data privacy. Nodal VPN solves this trade-off with a unique Hybrid Architecture: the lightweight control plane handles all user identity, 2FA, and zero-config distribution in the cloud (integrating seamlessly with Active Directory, Entra ID, and Google Workspace). Crucially, the heavy data plane remains solely on your on-premise infrastructure. This separation guarantees unmatched security, performance, and compliance, ensuring your sensitive network traffic never leaves your control while providing the management simplicity you need.
by Lee PainterThe shift to cloud-managed VPNs often forces IT administrators to choose between management convenience and data privacy. Nodal VPN solves this trade-off with a unique Hybrid Architecture: the lightweight control plane handles all user identity, 2FA, and zero-config distribution in the cloud (integrating seamlessly with Active Directory, Entra ID, and Google Workspace). Crucially, the heavy data plane remains solely on your on-premise infrastructure. This separation guarantees unmatched security, performance, and compliance, ensuring your sensitive network traffic never leaves your control while providing the management simplicity you need. - Help Me Help You: A Guide to Effective Technical Support
 by Lee PainterAs maintainers of commercial and open-source Java SSH APIs, our primary goal is to provide a stable, secure, and performant foundation for your applications. We love seeing the value-added solutions you build with our tools. When issues arise, we are committed to helping you resolve them as quickly as possible. When you reach out for… Read more: Help Me Help You: A Guide to Effective Technical Support
by Lee PainterAs maintainers of commercial and open-source Java SSH APIs, our primary goal is to provide a stable, secure, and performant foundation for your applications. We love seeing the value-added solutions you build with our tools. When issues arise, we are committed to helping you resolve them as quickly as possible. When you reach out for… Read more: Help Me Help You: A Guide to Effective Technical Support