- Benchmarking WireGuard: Why Your Data Plane Location is Critical for Speed
 by Lee PainterWireGuard is celebrated worldwide for its lean code base and superior speeds compared to legacy protocols like OpenVPN. But if your team is still facing sluggish remote access, the problem isn’t the protocol—it’s the architecture. The single greatest factor affecting VPN speed is latency, and latency is primarily determined by distance. While using WireGuard guarantees… Read more: Benchmarking WireGuard: Why Your Data Plane Location is Critical for Speed
by Lee PainterWireGuard is celebrated worldwide for its lean code base and superior speeds compared to legacy protocols like OpenVPN. But if your team is still facing sluggish remote access, the problem isn’t the protocol—it’s the architecture. The single greatest factor affecting VPN speed is latency, and latency is primarily determined by distance. While using WireGuard guarantees… Read more: Benchmarking WireGuard: Why Your Data Plane Location is Critical for Speed - Hybrid VPN: Cloud Management, Zero Data Traffic
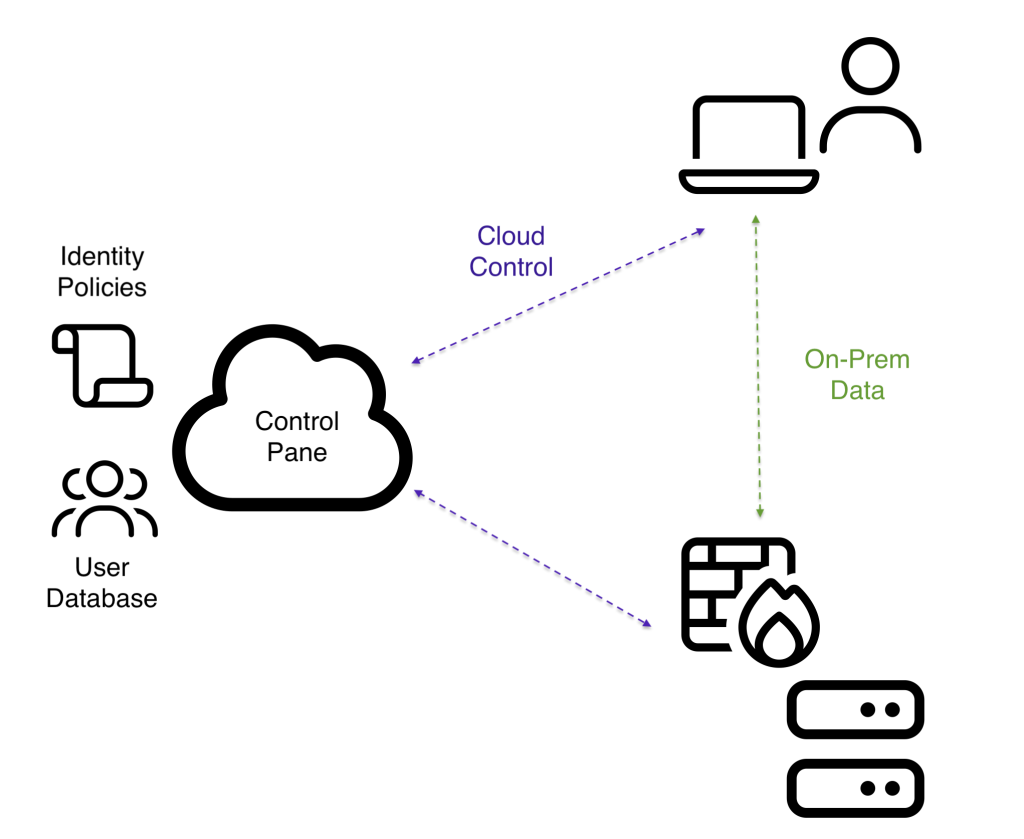 by Lee PainterThe shift to cloud-managed VPNs often forces IT administrators to choose between management convenience and data privacy. Nodal VPN solves this trade-off with a unique Hybrid Architecture: the lightweight control plane handles all user identity, 2FA, and zero-config distribution in the cloud (integrating seamlessly with Active Directory, Entra ID, and Google Workspace). Crucially, the heavy data plane remains solely on your on-premise infrastructure. This separation guarantees unmatched security, performance, and compliance, ensuring your sensitive network traffic never leaves your control while providing the management simplicity you need.
by Lee PainterThe shift to cloud-managed VPNs often forces IT administrators to choose between management convenience and data privacy. Nodal VPN solves this trade-off with a unique Hybrid Architecture: the lightweight control plane handles all user identity, 2FA, and zero-config distribution in the cloud (integrating seamlessly with Active Directory, Entra ID, and Google Workspace). Crucially, the heavy data plane remains solely on your on-premise infrastructure. This separation guarantees unmatched security, performance, and compliance, ensuring your sensitive network traffic never leaves your control while providing the management simplicity you need. - Help Me Help You: A Guide to Effective Technical Support
 by Lee PainterAs maintainers of commercial and open-source Java SSH APIs, our primary goal is to provide a stable, secure, and performant foundation for your applications. We love seeing the value-added solutions you build with our tools. When issues arise, we are committed to helping you resolve them as quickly as possible. When you reach out for… Read more: Help Me Help You: A Guide to Effective Technical Support
by Lee PainterAs maintainers of commercial and open-source Java SSH APIs, our primary goal is to provide a stable, secure, and performant foundation for your applications. We love seeing the value-added solutions you build with our tools. When issues arise, we are committed to helping you resolve them as quickly as possible. When you reach out for… Read more: Help Me Help You: A Guide to Effective Technical Support - Technical Report: Analysis and Mitigation of Paramiko’s Unbounded SFTP Prefetching
 by Lee PainterExecutive Summary A deep-dive technical analysis into server Out-Of-Memory (OOM) errors during SFTP transfers has confirmed that the default operational behavior of the Paramiko Python library is the root cause. This report details how Paramiko’s aggressive, unbounded prefetching mechanism, compounded by inefficient client-side window management, can create a denial-of-service scenario that exhausts server resources. This… Read more: Technical Report: Analysis and Mitigation of Paramiko’s Unbounded SFTP Prefetching
by Lee PainterExecutive Summary A deep-dive technical analysis into server Out-Of-Memory (OOM) errors during SFTP transfers has confirmed that the default operational behavior of the Paramiko Python library is the root cause. This report details how Paramiko’s aggressive, unbounded prefetching mechanism, compounded by inefficient client-side window management, can create a denial-of-service scenario that exhausts server resources. This… Read more: Technical Report: Analysis and Mitigation of Paramiko’s Unbounded SFTP Prefetching - Why you should not be using Personal Information for 2FA
 by Lee PainterIn the digital era, it’s important that we find ways to safeguard our data, and our methods to secure our accounts are continually advancing. A widespread yet increasingly problematic security measure is the use of personal questions, often termed “security questions.” While seemingly harmless, inquiries such as “What was your mother’s maiden name?” or “Where… Read more: Why you should not be using Personal Information for 2FA
by Lee PainterIn the digital era, it’s important that we find ways to safeguard our data, and our methods to secure our accounts are continually advancing. A widespread yet increasingly problematic security measure is the use of personal questions, often termed “security questions.” While seemingly harmless, inquiries such as “What was your mother’s maiden name?” or “Where… Read more: Why you should not be using Personal Information for 2FA